When Ransomware "attacked" the NHS
15th May 2017
It will surely come as absolutely no surprise or indeed news to anyone that the biggest topic in IT this morning is the so called "NHS attack". In this blog we're going to try and remove some of the confusing aspects of the incident and debunk some of the nonsense we've seen the media communicate. We'll also help you understand what you can do about this - either before or after it's too late!
Apologies in advance - this is a lengthy blog but we really do recommend you take the time to read it so you're better informed and can avoid your company becoming a victim of these incredibly successful campaigns.
Is this actually an attack that started with the NHS?
First off, let's cover "attack" - attack suggests someone has purposely picked someone (a company/organisation) and targeted them for this - that's pretty much guaranteed not to be the case. It just happens that the NHS is a really high profile organisation and the environment made it fairly easy for the malware to spread. However, this has been seen across companies across the world, as the reality it it's not targeted at someone - but simply anyone!
What is the malware for?
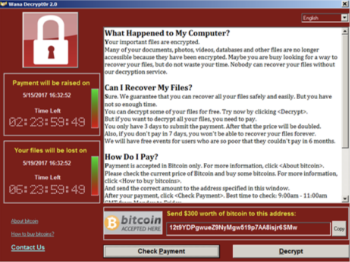
The malware is in the category known as ransomware - it quite simply takes an action that the authors hope will result in you handling over your money (converted into a virtual currency called Bitcoin) to get the files it encrypts back - eg they hold your data to ransom. It's actually very effective because despite the huge rise in this type of malware, people still do not take backups seriously, so there's a good chance data will be lost without paying up.
Who gets the money, and what is it used for?
It's pretty safe to say that this stuff is organised crime - the money goes to criminals and supports criminal activity and the lifestyles of those involved. There's nothing "legitimate" about the activity. Therefore if you're in the position that you feel you have no choice but to pay, you're ultimately helping to fund the very people responsible, which is why we couldn't recommend you avoid paying these ransoms if at all possible.
How do people get infected?
This malware starts like most of the other malware incidents we've seen over the last few years - it's almost always a simple case of someone opening an attachment from someone that is infected. It's also almost always an e-mail from someone you've never heard of - because this stuff is not targeted - it just uses spoofed address information and/or email addresses stolen from others online via various means.
In the typical ransomware we've seen thus far, when a "victim" opens the e-mail attachment, it will either take advantage of a vulnerability in the application that is opening the attachment, or will use normal, permissible features of the operating system or application to do what it wishes to do.
For the first type - where it takes advantage of a vulnerability in software, this is normally possible because a software defect is taken advantage of (known as an exploit), and allows something to happen that ordinarily should not be possible - for example accessing and writing files to a drive, or executing a command that's normally off limits. There are 2 real categories of these - known vulnerabilities for which there are patches - updates from the software vendors, and those which are either not patched OR are not yet known issues (often known as a 0-day exploit) - and thus there is no current fix. It's for this reason that it is important you consider all applications as well as just Windows or your operating system for updates as this helps reduce how vulnerable you are.
The second method of infection...
What sets this ransomware incident apart from the rest is that it has a second infection method. It's this second method that is being used very successfully - but it is important to understand that in most cases this happens AFTER the first method was used - although it IS possible to become infected if you have an insecure network setup that has one or more systems with direct internet access and specific ports (services) open to the world.
The second infection method takes advantage of other vulnerability in the Windows File Sharing functionality - known more technically as "SMB v1" - the vulnerability was fixed by Microsoft in March 2017, for all versions of Windows (except Windows 10 which is not vulnerable to this particular attack). However, users of Windows XP would (until this weekend) only have been able to patch this issue if they had a special support contract with Microsoft as it has not been making publicly available patches accessible for a long time now (because Windows XP is no longer supported without these special support contracts).
It's clever because it actually can use 2 different vulnerabilities, and those vulnerabilities allow it to copy itself onto another computer system, and then repeat the same infection, encryption and replication to another system behaviour - so it's really easy to see how fast it can move across a network, especially because it's clear that most systems are vulnerable, are not fully up to date etc. It's also clever because it only needs one victim and it can then get everything connected to that network - unlike traditional ransomware which can often get one person (and sometimes some additional damage - but not on this scale).
What does it actually do?
The malware encrypts data - documents etc - with a list of specific file types it is interested, including all the common formats such as Microsoft Word documents. Encrypting takes your original document and "scrambles" it in such a way it cannot be read normally anymore - and to then read it, you need the decryption key (a bit like a password). It's able to encrypt everything on your own PC (and if you run your computer so that you have full admin rights, it can do a considerably more thorough job - which is why we absolutely recommend against doing this!).
That isn't enough for modern ransomware - they know that you might well have a USB Drive, Flash memory drive connected (or several), and that you might also have "mapped drives" to other remote resources - such as a share on your Servers or a NAS where your data will be. It'll happily go through all of these and encrypt the files you've got there too. This is one of the reasons that this is so incredibly effective - because despite our advice otherwise, it's all too common for people to rely on a "backup" that is connected al the time or entirely vulnerable.
The full list of file types this particular variant is believed to tackle is listed below:
.der, .pfx, .key, .crt, .csr, .p12, .pem, .odt, .sxw, .stw, .3ds, .max, .3dm, .ods, .sxc, .stc, .dif, .slk, .wb2, .odp, .sxd, .std, .sxm, .sqlite3, .sqlitedb, .sql, .accdb, .mdb, .dbf, .odb, .mdf, .ldf, .cpp, .pas, .asm, .cmd, .bat, .vbs, .sch, .jsp, .php, .asp, .java, .jar, .class, .mp3, .wav, .swf, .fla, .wmv, .mpg, .vob, .mpeg, .asf, .avi, .mov, .mp4, .mkv, .flv, .wma, .mid, .m3u, .m4u, .svg, .psd, .tiff, .tif, .raw, .gif, .png, .bmp, .jpg, .jpeg, .iso, .backup, .zip, .rar, .tgz, .tar, .bak, .ARC, .vmdk, .vdi, .sldm, .sldx, .sti, .sxi, .dwg, .pdf, .wk1, .wks, .rtf, .csv, .txt, .msg, .pst, .ppsx, .ppsm, .pps, .pot, .pptm, .pptx, .ppt, .xltm, .xltx, .xlc, .xlm, .xlt, .xlw, .xlsb, .xlsm, .xlsx, .xls, .dotm, .dot, .docm, .docx, .doc,
[Thanks to
Talos Intelligence]
As well as the encrypting of files (which we see with all the ransomware variants although the file types vary, as does the encryption used and whether it runs through your network drives etc), this second method of infection is attempted once it's on a computer. The malware determines which other computers are on the network, and then just tries to use the exploits and vulnerabilities - it has 2 different options to try, and if successful repeats the entire process. Therefore only one user would typically need to fall foul of the dodgy attachment, or you only need one badly configured computer, server or similar which is internet accessible and you're going to have a lot of pain.
What does this have to do with the NSA?
The exploits being used - to replicate to other computers and as the second infection option are based on "toolkits" (vulnerabilities kept secret and turned into software used to deliberately hack/infiltrate a computer system) that the NSA had found/developed. They've had knowledge of these exploits for quite some time, but they did not want to disclose them as they were useful to the organisation in compromising those those computer systems they wanted to get into. This came to light recently when those toolkits got leaked (someone else disclosed them without authority from the NSA). This put the vulnerabilities in the public domain so they could be used by anyone that fancied taking advantage of the same vulnerabilities the NSA has been using. It isn't the case (at least, there is no proof) that the NSA itself created the malware - and indeed it is pretty unlikely.
Microsoft have written about the attack and specifically the situation with the NSA on a blog from the Chief Legal Officer here.
Did Microsoft release a fix for this and when?
Once the vulnerabilities became known about Microsoft did indeed release patches for the issues to stop them being exploited, and these came in March 2017, as part of the Microsoft monthly patch releases (often called Patch Tuesday). Those fixes came out for Windows Vista, Windows 7, Windows 8.1 and Server 2008, server 2008 R2, Server 2012 and Server 2012 R2. Importantly though, they did not release the updates in March for Windows XP, Server 2003 and Windows 8.0 as they do not support any of these operating systems any longer (Windows 8.0 is not supported as they expected everyone to have moved to Windows 8.1). Support for these is technically available, and patches did exist - but you had to have a special and very expensive agreement to receive them.
On Saturday, Microsoft backed down from this policy and has made patches available publicly for Windows XP, Windows Server 2003, Windows 8.0 etc as it recognises the seriousness of the incident, but is reminding people to stop using these unsupported operating systems.
So is Windows XP to blame?
Not exactly, although some would have misguidedly led you to believe it is the case. Windows XP was - at least until the special release of a patch on Saturday still vulnerable in the majority of cases as no support agreement exists. Microsoft has completely stopped supporting this operating system except in very special cases and anyone still using XP should in theory have stopped using it, although there are a number of reasons and organisations still using XP and Server 2003 in particular (including the NHS - but by no means only them!). So it does mean if you had XP without a special support arrangement (and had already applied the fix) you had more exposure.
What can we do to protect ourselves from this and indeed other such incidents?
Firstly, you need to ensure you have a patch installed that protects from the particular vulnerability that is being exploited on EVERY computer - that's every single desktop, laptop and server system that runs Windows XP, Vista, 7, 8.0, 8.1 and Server 2003, 2008, 2008 R2, 2012 and 2012 R2 without exception. This malware spreads using the issues addressed in patches so installing these will significantly reduce any ability to spread and reduce your exposure. VPW Technical Support can assist clients with this - contact the Support Team - and if you're not currently a client we're happy to discuss our support plans to assist you of course.
There are a number of things you should be doing:
1) Download the Patches and Install them - everywhere!
Download the patches application for your operating systems here:
https://technet.microsoft.com/en-us/library/security/ms17-010.aspx
This only really helps (currently) with the malware incident that has been widely publicised, but it is entirely possible other similar variants will arise using the same flaw, so get these installed NOW.
2) Make sure you have Anti-Virus Software on every system
We STRONGLY recommend a centralised AV system where feasible that can report incidents happening on any system, provide rapid updates and we also strongly recommend you use a paid for product which receives more frequent updates. Free products generally have poor update cycles and other limitations (not an absolute rule, but AV is cheap compared to the hassle it creates!)
3) Get a service that pre-filters your e-mail
Our service - the Cloud Anti-Virus & Anti-Spam Filtering service significantly reduces your potential exposure - whilst it cannot like any anti-virus technology be 100% flawless, we remove huge volumes of malicious e-mail every single day so you'll seriously reduce the number of opportunities to get infected with this. It's not expensive and is an easy upgrade to your existing e-mail service.
In response to this incident, we're offering FREE setup on Annual Payment Plans to help you protect your business against this issue.
4) Train people - DO NOT OPEN ATTACHMENTS
This is by far the most common way people get infected. They open an attachment that has an innocent looking and sounding attachment. Don't open them, be very suspect, if you see an attachment from someone you think you know contact them first, and check it really was them. If it is from someone you do not know, just don't take a chance. In almost all cases we see of this, we find that someone somewhere opened something they shouldn't!
It's especially important to remember that some of the most common cases of dodgy attachments use variants of the Microsoft Office document formats - such as DOCM or XLSM which will prompt - by default - Office to warn you about allowing the documents advanced features to be used. We recommend that you absolutely NEVER, regardless of who the message is supposedly from open those messages, and indeed where practical we recommend you block receipt of those message types entirely.
5) Backups - You need a really good backup service
We've published many blog's before on the subject of backups, but our current recommendations remain as they've always been - you MUST have robust backups in place. We absolutely strongly recommend our Remote Backup for Small Business service. We don't recommend any sort of "backup" that involves data being copied to drives within your system, network or otherwise kept in an available state. Our Remote Backup service securely takes copies of your data off-site in such a way that even if you are infected and every file is encrypted we have a good copy of your data to recover you from.
Our service is a low cost, effective way to keep your data safe, and can backup all document types, with options for more advanced services - for example SQL Server and Exchange available too.
In response to this incident, we're offering 50% off setup on Annual Payment Plans to help you protect your business against this issue.
6) Do not give every user admin access
It might be considered a "hassle" but there is a very good reason you should never let users routinely operate in administrator mode (and really they shouldn't know the logins for administrators either). This helps prevent or reduce your chances of a problem. We've seen plenty of cases where customers that follow our guidance and have a fully managed installation from us are protected simply because the malware they receive doesn't work, or has considerably lower impact without admin rights. This isn't always the case - especially if the malware is using an exploit that can bypass this but it makes a big difference. Often the computer popping up unexpectedly is a good sign something is potentially amiss and helps rapidly identify the problem.
Further, non-admin users often have more limited access, so encryption can be limited to fewer files, directories and so on, or may prevent some types of replication from operating.
7) Get Proactive about installing security updates
It's really important you get Security Updates onto your systems and nothing demonstrates the need for this more clearly than this ransomware incident. To help, we offer a number of Proactive Maintenance services that ensure your systems stay up to date. They include our team managing and installing updates that are checked and approved for installation to help you balance compatibility and downtime issues caused by problems with patches against the need to keep your systems secure.
If you need assistance either to protect your business against this and other similar risks, or you have already been infected and need help, please do not hesitate to contact us:
Existing Customer with Pre-Paid or Committed IT?
Contact our HelpDesk and we can assist you - please refer to your Welcome Packs or our Help & Support section for the contact information for your account.
New Customer or Existing Customers without a Support Plan?
Please contact us today - 01392 950 950 and ask how we can help you